Contents
Your customers place their trust in you to protect their data. Just one security breach can break this trust right away. When vulnerabilities pop up, they become perfect targets for attacks. If your security controls are weak, your systems are left wide open. Plus, unauthorized access doesn’t announce itself — it’s quietly sabotaging your systems before you even realize it.
In this article, we’ll discuss some key security practices that every DevOps team should have in their toolkit — firewalls and identity access management. These are two essentials for keeping your development environment safe and sound.
What Is a Firewall?
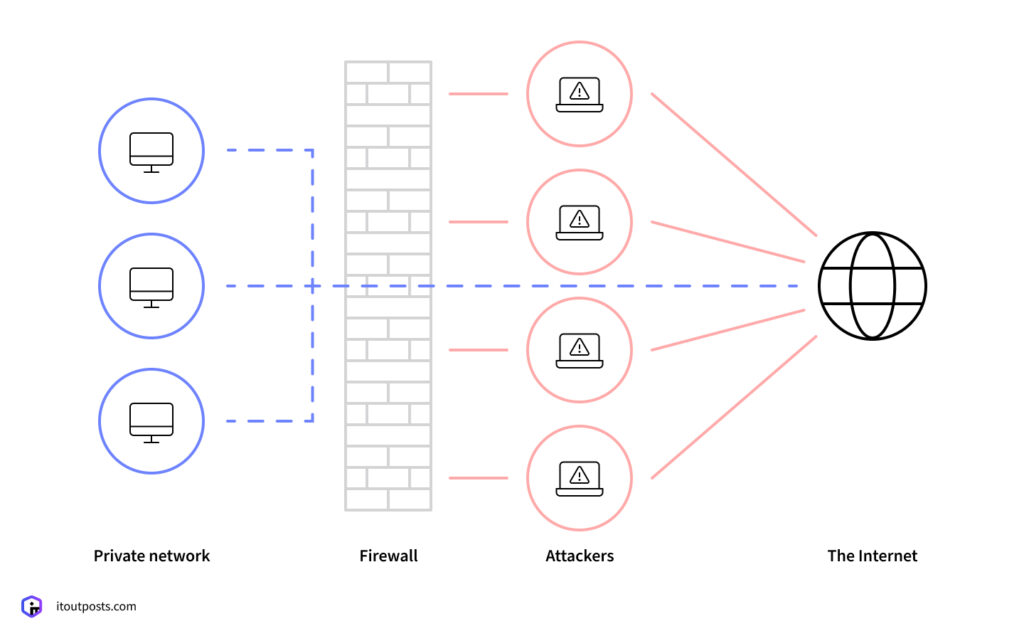
Every time you deploy code, there’s a lot of unseen digital traffic flowing in and out of your systems. And firewall aims to be the security checkpoint for this traffic.
It examines each data packet trying to enter or leave your network and makes quick decisions: allow or block, based on rules you’ve set up. You might have rules, like “block all traffic from this suspicious IP address” or “allow secure connections to our database, but only from our application servers.”
How IT Outposts Sets Up Firewalls
When we build our network infrastructure, we start with a foundation of security by design. We place everything within a virtual private network (VPN), but that’s just the beginning of our defense strategy.
Our setup includes carefully configured network access control lists (ACLs) that determine which traffic is permitted or denied at the network level. This way, we can block any unwanted traffic before it even gets close to our network’s perimeter.
For example, our application running on EKS needs to communicate with the database. Even though these components are on different subnets within the same network, we allow traffic to flow freely between them. Still, we make sure to set up restrictions using security groups. We design these groups so that only our EKS cluster can connect to the database.
Alternatively, we can create a bastion host — a secure server inside our network that has limited access through specific IP addresses and ports. Users connect to this bastion first, and then it gives them access to the database.
Our team uses this strategy for every service, locking them down with security groups, roles, and port settings. Each service gets its own role that has specific permissions defining which services it can communicate with. Overall, we only allow access where it’s truly necessary, and this is our golden rule at IT Outposts.
And if we need to broaden access later, it’s easy to update the security groups to expand those permissions. This is how we effectively implement firewall protections in our clients’ infrastructure.
Benefits of Firewalls
Strong firewall configurations in your DevOps environment are critical to keeping this environment protected. And once you set them up, expect the following benefits:
- Intrusion prevention. Firewalls block unauthorized access attempts before they ever get near your sensitive systems or data.
- Lateral movement prevention. Even if an attacker manages to breach one system, well-configured firewalls can stop them from moving laterally to other systems in your network.
- Compliance support. Firewalls play a big role in helping you meet regulatory requirements. They make preparing for audits easier and can lower your compliance risks. We saw this in action when we helped OneDayBundle, an e-commerce fulfillment company, get access to the Amazon Selling Partner API. Firewall implementation was one of the components of their security strategy that enabled them to pass Amazon’s rigorous security review process.
What Is an Identity Access Management?
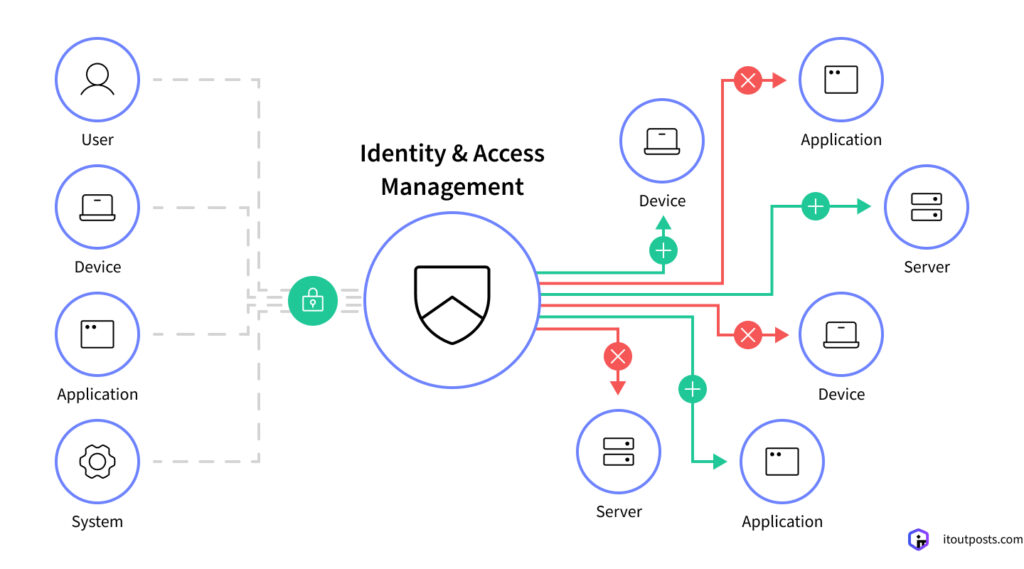
Identity access management, or IAM for short, is a comprehensive framework that controls and manages digital identities and their access to resources within an organization. It’s not just about giving people access — it’s about ensuring they get the right level of access. Therefore, your IAM strategy must answer three important questions:
- Who are you?
- What can you access?
- What can you do with that access?
How IT Outposts Implements Identity Access Management
We offer our clients an approach where we create different groups with specific permissions. When clients want to give their employees access, all they need to do is create a user and put them in the right group. Each group is set up with permission sets that are personalized for particular roles.
For example, we might add a QA specialist to a read-only group. This gives them visibility into all services but limits them to viewing information — they can check service operations, statistics, metrics, and other monitoring data without making changes.
By default, our team typically establishes several standard groups:
- Administrators with full access
- Read-only users with viewing privileges only
- Listing group specifically for service accounts
The listing group serves an important organizational purpose — when we need to create users that provide access to third-party programs (like external monitoring tools that need account access), we place them in this dedicated service account group.
Benefits of Identity Access Management
Here’s how IAM can improve your security and operations:
- Enhanced security posture. IAM helps cut down the chances of unauthorized access by making sure each user only has the permissions they need to do their job.
- Less work for admins. Administrators can quickly set up, change, or remove access rights across different systems at once. This way, you don’t have to manage permissions on individual platforms.
- Simplified onboarding and offboarding. New employees can get access to the systems they need right away when they join, and when someone leaves, you can revoke their access with just one action.
Build Stronger Boundaries with IT Outposts!
Investing in solid security practices now will pay off in the long run. You’ll protect your data, keep your customers’ trust, and be able to act quickly without taking on unnecessary risks.
Fortunately, implementing robust firewalls and IAM doesn’t require a significant investment if you choose our AMIX. It’s a pre-built infra with comprehensive security measures, along with other essential DevOps practices like infrastructure as code, monitoring, and more.
Explore AMIX Infrastructure and contact us for a complete solution designed by professionals.

I am an IT professional with over 10 years of experience. My career trajectory is closely tied to strategic business development, sales expansion, and the structuring of marketing strategies.
Throughout my journey, I have successfully executed and applied numerous strategic approaches that have driven business growth and fortified competitive positions. An integral part of my experience lies in effective business process management, which, in turn, facilitated the adept coordination of cross-functional teams and the attainment of remarkable outcomes.
I take pride in my contributions to the IT sector’s advancement and look forward to exchanging experiences and ideas with professionals who share my passion for innovation and success.