Contents
Firewalls and VPNs are crucial for security. But they’re not enough on their own. Unless security is built into how software is developed and delivered, these defenses only provide partial protection. That’s where DevSecOps comes into play and integrates security at each phase of your DevOps pipeline.
In this article, we explain what DevSecOps is and how it differs from DevOps. We also discuss its importance and highlight the best methods that can help you implement DevSecOps effectively.
What Is DevSecOps?
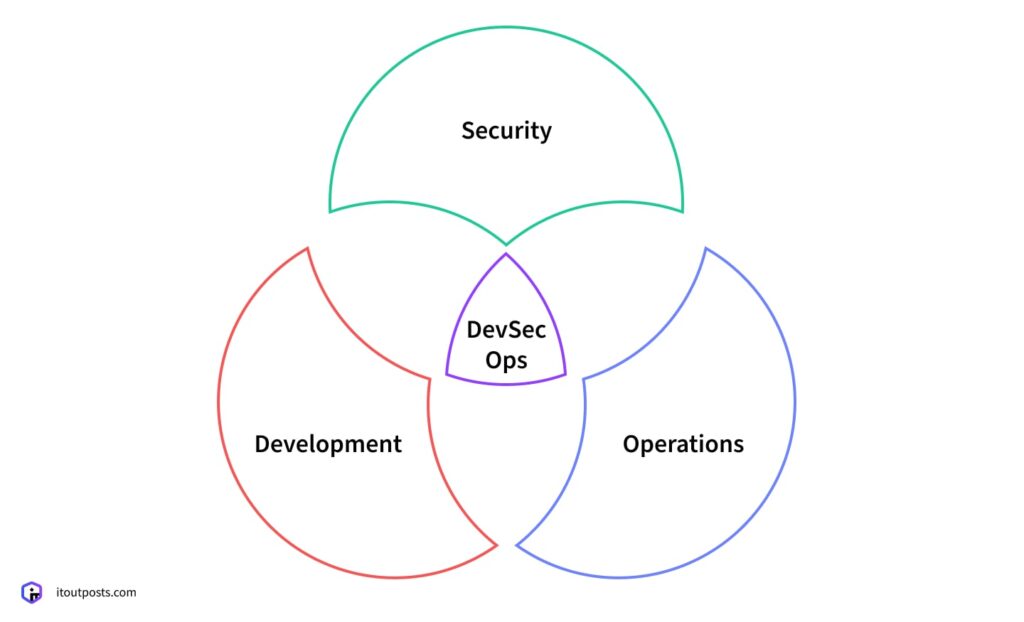
DevSecOps is an approach that extends DevOps by integrating security practices from the very start of the software lifecycle. In DevOps, a significant goal is removing obstacles between developers and operations, which allows teams to work faster and release more frequently. DevSecOps is built on this concept, but also adds the security part into the equation and poses a question:
How can we maintain the speed and frequency of releases that DevOps makes possible without leaving security behind?
The solution is to incorporate security within the process itself, or put simply, shift left (so that security isn’t treated as a separate stage after development).
To understand how this works, let’s refer to the DevOps pipeline first. DevOps provides us with the following framework: plan, build, test, release, deploy, and operate.
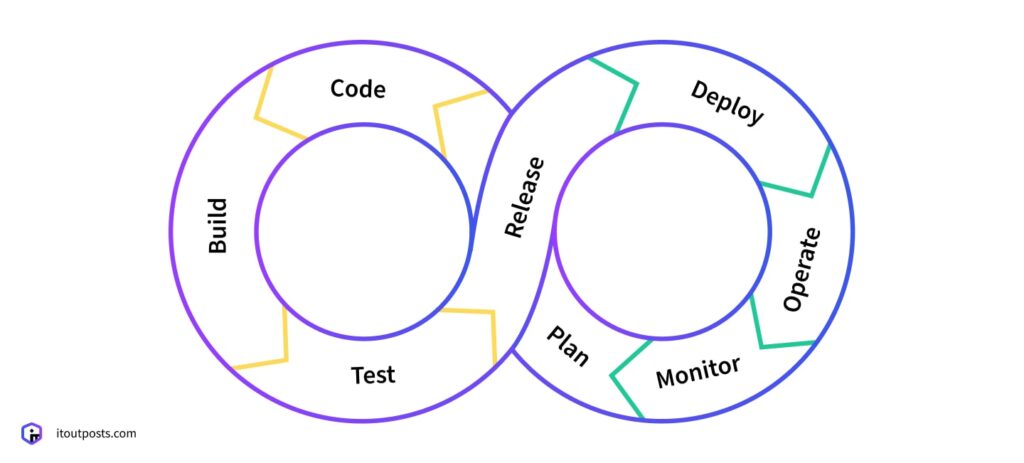
Now, let’s think about the same pipeline but with security measures woven into it. This creates a DevSecOps pipeline.
What Is a DevSecOps Pipeline?
So, in the DevOps pipeline, emphasis is placed on speed and automation: developers push code, builds are created, and releases progress towards production.
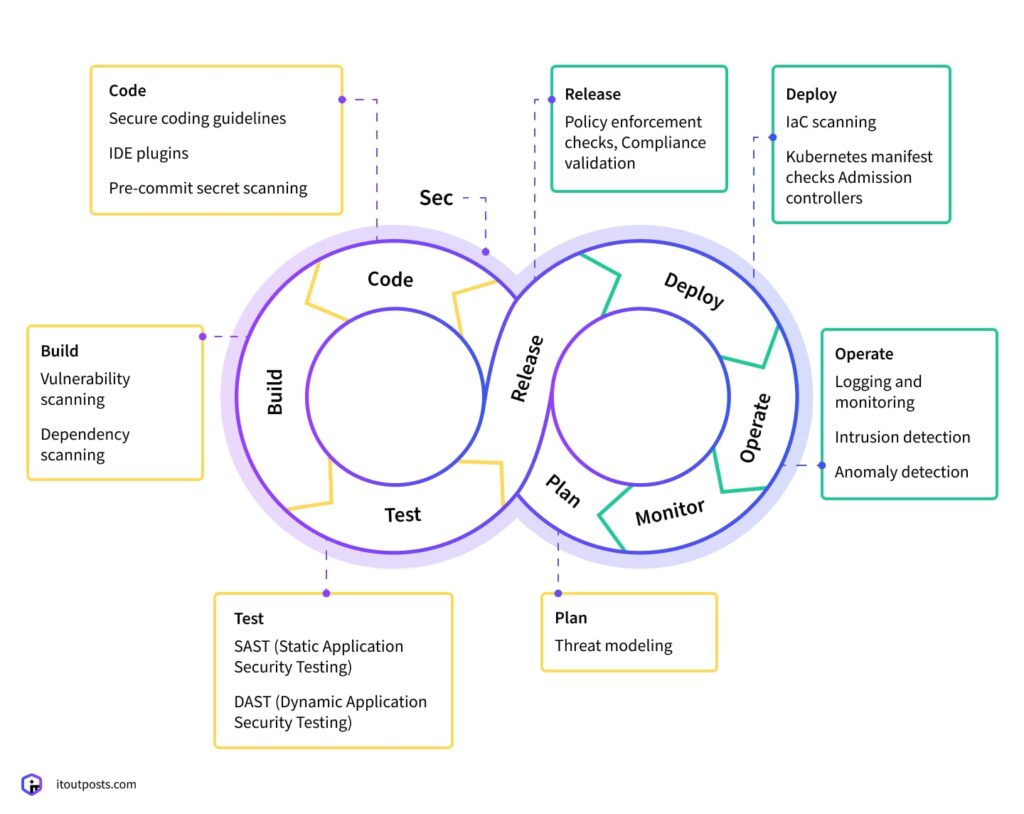
In a DevSecOps pipeline, the same actions occur; however, each stage involves a security checkpoint. At these checkpoints, automated checks are triggered (for example, secret scanning when code is committed) and happen concurrently with development and operations.
Here’s how it looks in practice:
- Plan. At this stage, security goals are defined together with business and technical goals. Here, threat modeling is used to predict potential attack routes and create defenses against them.
- Code. While coding, developers follow secure coding guidelines and use tools like IDE plugins that highlight risky code patterns as they write. In addition, pre-commit hooks inspect for any secrets that might have been accidentally included in the codebase.
- Build. Before the code compiles, it’s checked for any vulnerabilities. Also, dependency scanning makes sure that libraries and packages from third parties don’t bring in known risks, such as outdated versions.
- Test. Security tests are performed along with functional tests. For instance, Static Application Security Testing (SAST) is used to identify weaknesses in the source code, whereas Dynamic Application Security Testing (DAST) simulates real attacks against the latest build of the app, running in a test or staging environment. The goal is to check how the updated app with new code included responds to malicious requests.
- Release. Before packaging, policy enforcement tools verify that all required security checks have passed. Only artifacts that fulfill both compliance and basic security requirements can proceed.
- Deploy. When you deploy, infrastructure-as-code templates and Kubernetes manifests are checked to find any misconfigurations. Admission controllers can stop deployments that don’t adhere to security policies.
- Operate. Logging and monitoring systems check for signs of intrusion, privilege escalation, or unusual traffic. Security tools used during operation can identify and block suspicious behavior in containers and cloud environments.
So here’s how these security measures fit into the DevOps pipeline, creating the DevSecOps pipeline:
Why DevSecOps Is Important
As software evolves rapidly, so do attack methods. DevSecOps is important because it ensures that security keeps up with delivery. This way, you don’t address problems post-launch but identify and protect your product against potential internal and external threats at the early pipeline stages.
DevSecOps lets you close common gaps, like unsafe code, vulnerable dependencies, and misconfigurations, before they turn into entry points for attackers. Finally, with monitoring tools integrated, it assists in detecting and reacting to actual threats swiftly.
How to Implement DevSecOps Successfully
For DevSecOps to be effective, you require both proper technical bases and cultural changes. Below are some best practices that will assist you in implementing DevSecOps.
1. Implement CI/CD (If You Haven’t Yet)
DevSecOps requires a dependable route for production. CI/CD provides this route. Each code change, whether it’s a bug fix or a new feature, will follow the same process: build, test, release, and deploy. And since this route is uniform, you can place security checks at every stage and be certain they will run each time.
2. Ensure Automation
DevSecOps is an extension of DevOps. And DevOps, at its core, is about automation. CI/CD pipelines are already a big part of this automated process. However, for security steps to function regularly, automation has to cover the wider DevOps framework as well.
DevOps automation also involves infrastructure as code (IaC) for setting up environments, configuration management to maintain system consistency, container orchestration for service scaling, automated monitoring to track production, and more. Security checks are only reliable when the underlying processes are automated.
3. Prioritize Threat Modeling
Threat modeling is an effective method to incorporate security in planning. It’s about asking questions, like:
- What are the possible things that could go wrong?
- How can an attacker potentially cause damage?
- Where is sensitive data exposed?
When planning a new release, your team should outline potential risks before coding, as it’s much more difficult to correct a design defect after a release than to make changes at the stage of preparation. Also, threat modeling helps you change the way of thinking: security isn’t just something you test for, it’s something you design for.
4. As You Shift Security Left, Shift Culture with It
As we’ve already found out, technically, shifting security left means conducting security checks as near as possible to the point where code is created.
Yet, this shift must happen not only technically but also culturally. It’s necessary for developers to view security as a component of their job. This can be achieved by providing them with real-time feedback on potential risks in their work. For instance, with the above-mentioned IDE plugins.
Training also plays a role. Practical sessions on secure coding practices will make your dev team more comfortable treating security as part of their everyday work.
Secure Your Pipeline with IT Outposts
The true power of DevSecOps lies in the fact that it doesn’t require creating new security measures for each release. Once the base is established, you continually reap its benefits. You identify weaknesses early on, lower the risk of breaches, and worry less about keeping a fast delivery pace without compromising safety.
IT Outposts can assist you in creating this base and integrating DevSecOps into your processes from the beginning. With our AMIX, a ready-made infrastructure setup, you get a secure, pre-configured solution that accelerates your time to market, saves engineering hours, and gives you the confidence to scale.
Get AMIX at no cost and contact us to discuss how your team can effectively implement DevSecOps right from the start!

I am an IT professional with over 10 years of experience. My career trajectory is closely tied to strategic business development, sales expansion, and the structuring of marketing strategies.
Throughout my journey, I have successfully executed and applied numerous strategic approaches that have driven business growth and fortified competitive positions. An integral part of my experience lies in effective business process management, which, in turn, facilitated the adept coordination of cross-functional teams and the attainment of remarkable outcomes.
I take pride in my contributions to the IT sector’s advancement and look forward to exchanging experiences and ideas with professionals who share my passion for innovation and success.