Contents
Secrets form the backbone of your security setup. Passwords, API keys, certificates, and tokens control access to your most sensitive systems and data. Yet, even with their critical importance, managing these secrets is often ignored in discussions about cybersecurity.
Ignored since secret management isn’t about direct security configurations but rather about how we transfer data. Still, there are plenty of ways secrets can be exposed, and the consequences can be catastrophic. If credentials are leaked or not secured properly, attackers can gain access to information that affects your customers.
This article explores the principles, practices, and tools of effective secret management. We’ll examine why traditional approaches fall short and what a modern secret management strategy looks like.
What Is Secret Management?
Secret management is how organizations handle sensitive credentials. It’s the system for creating, storing, sharing, changing, and removing passwords, API keys, and other access credentials.
With the help of this approach, you answer the question: how do we give the right secrets to the right systems and people and keep them away from everyone else?
Common Security Pitfalls in Secret Management
And depending on your approach, the answers can sometimes be less than ideal. For example, a lot of organizations end up falling back on some not-so-reliable methods for secret management. Here are a few of them.
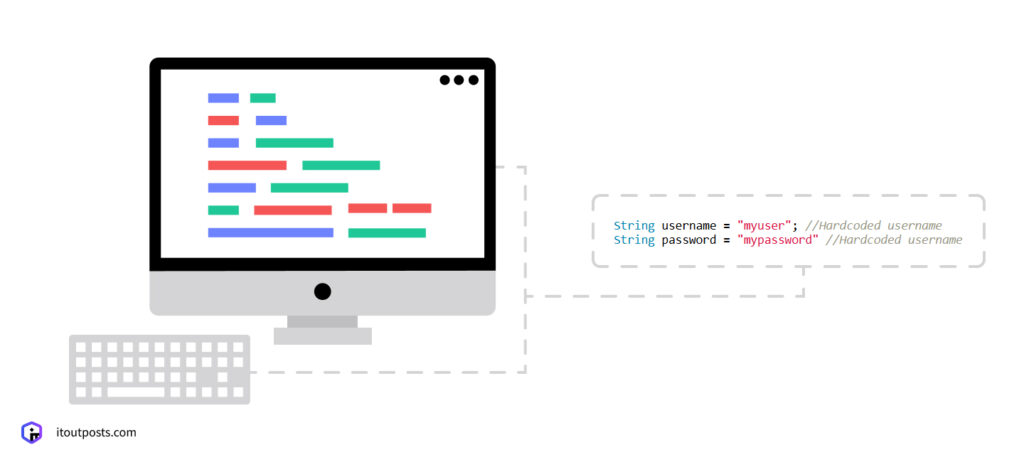
Hardcoded Secrets
One common mistake is when developers hardcode secrets directly into their code. This means they write passwords, API keys, or access tokens right into the application’s source code. While this might seem convenient during development — after all, the app works right away without extra setup — it comes with huge security risks.
When these hardcoded secrets are stored in a repository, they become accessible to anyone with access to that codebase. If a hacker gets into the repository, they can find all those credentials at once. Plus, changing hardcoded secrets is difficult since you have to modify the code and redeploy the application, which discourages regular password changes.
Configuration Files
Some developers store secrets in configuration files separate from their code. While this keeps credentials out of the source code itself, these files often end up committed to Git repositories alongside the code. The application still references these files to retrieve secrets, so they become pretty obvious targets.
It’s a bit of an improvement, but still far from secure. If someone gets access to the repository, they can easily pull the secrets from these files.
Environment Variables Are a Stronger Alternative
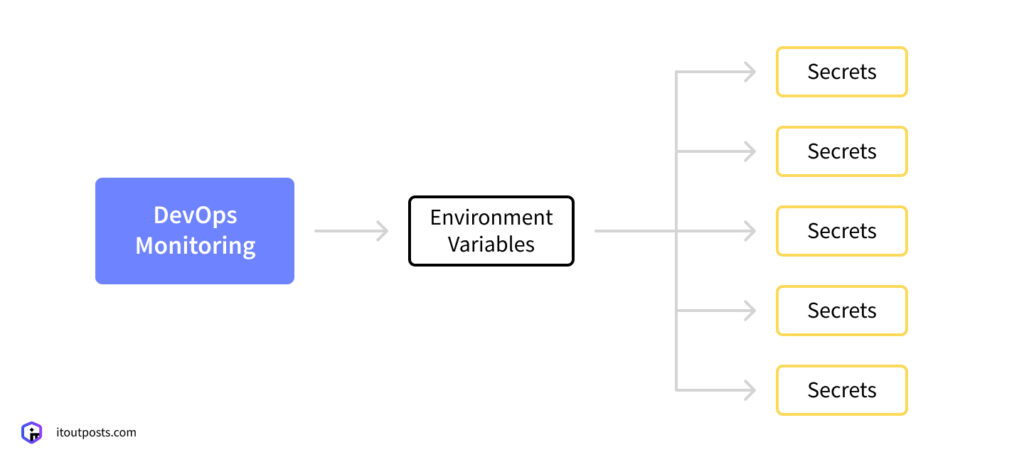
To steer clear of potential issues, it’s best to pull secrets from environment variables instead of files. This is a more secure option.
The perfect scenario is when you set a secret with its value directly in your Linux console on your local machine. Then, you can run a command that uses that secret name, which will pull the secret from your local environment rather than from any file. This way, you won’t accidentally push it to a repository, and no one else can access it unless they’re connected to your computer and know the value.
In a production setting, when you type “API key equals” along with the key name, it happens automatically in a local, isolated, and secure setup. We use specific tools to transfer these values, so you won’t find them written down anywhere — they’re kept private.
Then, you can take these values from secret storage and send them to the local environment where the application is deployed. This is how your secrets remain safe.
In addition to encrypting these secrets, we also set up an External Secret Operator inside the cluster. This connects to Amazon Secret Manager, retrieves all these secrets, and breaks them down into key-value pairs (like an API key as the key and the password as the value). It processes them and delivers them to the environment.
And when you launch an application, you simply inform it which specific secret it’s using. The application will automatically know the hidden key associated with that secret and how to access the necessary resources.
Benefits of Organized Secret Management
Taking a structured approach to managing secrets goes beyond keeping your credentials safe (although it’s already a great achievement). Let’s explore all the benefits.
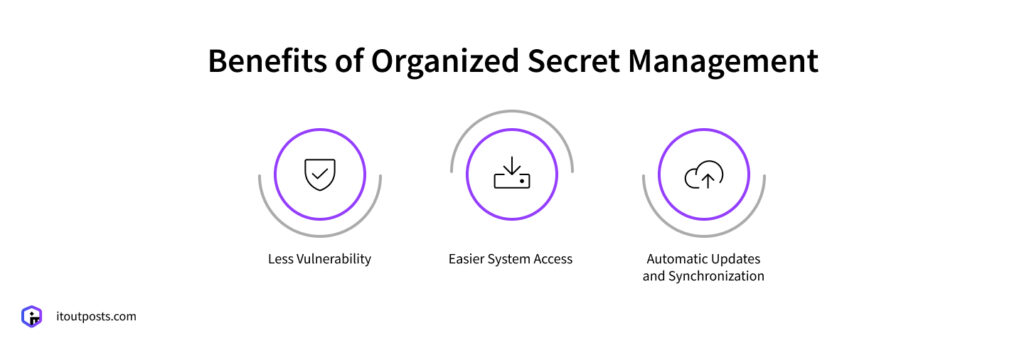
Less Vulnerability
Instead of spreading secrets across code, configuration files, and personal computers, you centralize them in a secure vault, which minimizes the chances of a breach. This way, if one thing gets compromised, your entire system doesn’t go down with it.
Easier System Access
Development teams can no longer waste precious time digging through documentation, messaging coworkers, or juggling multiple systems just to find the right credentials. They can easily request access to the secrets they need, exactly when they need them.
Automatic Updates and Synchronization
We also set up a reloader that monitors any changes or new secrets. When it detects a change, it automatically restarts the deployment. This way, your application starts using the new values right away. If someone updates a secret, they just add it to the manager, and voilà — no extra steps required; everything updates smoothly.
This approach is beneficial because it makes everyone’s job easier and prevents issues where someone changes a secret without telling anyone else, only for another engineer to find out they can’t access a system anymore. But in your system, everything’s in one spot, and everyone knows where to find it. They can trust that the exact secret they need is being used in their environment.
Secrets Must Stay Secrets
With proper secret management, you address multiple critical aspects. First and foremost is security. You make sure your sensitive information isn’t accessible to anyone who shouldn’t have it. Next, it’s all about having a more organized and optimized management process.
Additionally, Amazon Secrets Manager offers versioning capabilities. This is handy when you have multiple team members working on the same secrets. If one person updates a secret and then someone else makes an additional change, versioning allows you to go back to earlier states easily. Without it, that could be harder.
Our AMIX package includes a comprehensive secret organization. You can be confident knowing that your infrastructure is secure and your data is well-protected from the start. Want to learn more about AMIX? It’s a pre-built infra you can get access to immediately and at no cost. Contact us for more details.

I am an IT professional with over 10 years of experience. My career trajectory is closely tied to strategic business development, sales expansion, and the structuring of marketing strategies.
Throughout my journey, I have successfully executed and applied numerous strategic approaches that have driven business growth and fortified competitive positions. An integral part of my experience lies in effective business process management, which, in turn, facilitated the adept coordination of cross-functional teams and the attainment of remarkable outcomes.
I take pride in my contributions to the IT sector’s advancement and look forward to exchanging experiences and ideas with professionals who share my passion for innovation and success.