Contents
“Hope for the best, prepare for the worst.” This is a great mindset for any business to have, especially given that system failures aren’t rare. Organizations report facing about 86 outages each year on average, and more than half experience disruptions on a weekly basis.
Disaster recovery planning allows you to get ready for the worst-case scenarios, like hardware crashes, cyberattacks, natural disasters, human errors, and any other events, and recover your systems quickly.
Yet, disaster recovery shouldn’t be viewed as purely a technical concern. It must be a core part of your business contingency plan. The choices you make should balance potential losses with the cost of protecting against them.
That’s why in this article, we’ll look at disaster recovery planning as a strategic business decision and share the five core aspects we rely on to get systems (and the business) back online, fast.
What Is a Disaster Recovery Plan?
A disaster recovery plan (DRP) is a guideline that outlines the procedures an organization will implement to restore its IT infrastructure and critical business functions after a disruption.
A typical DRP includes:
- Critical system identification
- Recovery strategies (backup and restore/mirroring)
- Step-by-step recovery procedures
- Communication flow plan with team roles and responsibilities
- Testing schedule and protocols
The consequences of not having this plan when it’s needed the most can be far-reaching:
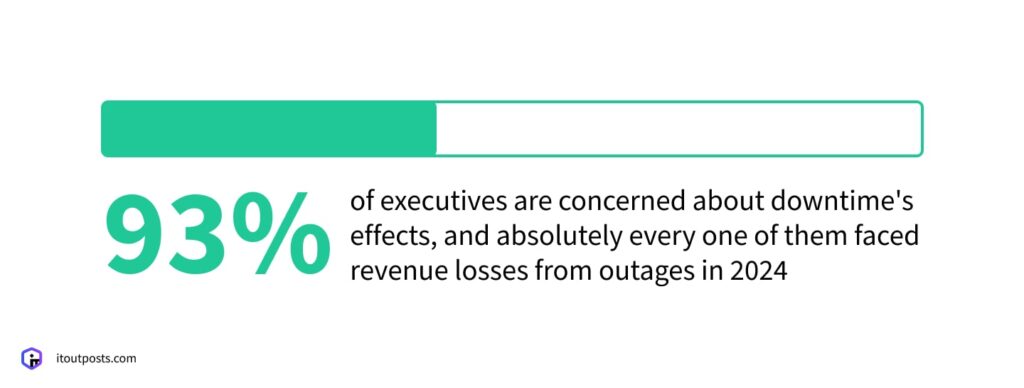
- Financial losses. Financial loss is perhaps the first and immediate consequence. When a business is offline for an extended period, it’s unable to generate revenue. For small to medium-sized businesses, this can be an existential threat. According to the State of Resilience 2025 report, 93% of executives are concerned about downtime’s effects, and absolutely every one of them faced revenue losses from outages in 2024.
- Irreparable data loss. A disaster would also mean that some data is lost for good. It may include customer details, financial records, intellectual property, and other information. No amount of money can recover data that wasn’t backed up.
- Damage to business reputation. A brand that is seen as unreliable in regard to protecting consumer data will struggle to attract new customers and retain existing ones.
- Regulatory penalties and legal issues. Depending on your industry, data breaches and outages can lead to hefty fines and lawsuits. Without a solid plan to safeguard sensitive information, businesses might face serious financial losses and damage to their reputation.
Likely, everyone has heard of, and perhaps some were even affected by, the 2024 outage caused by a faulty security update from CrowdStrike, which impacted Windows endpoints that are running the CrowdStrike Falcon agent. This incident is a reminder that system failures can bring down businesses in an instant.
Thousands of canceled flights, crashed payment systems… The financial and reputational damage was immense—millions and even billions of dollars. And this relates to both CrowdStrike and Microsoft, as well as the countless companies that relied on their services and couldn’t operate for hours or even days.
Disaster Recovery Plan as Part of Business Contingency Plan
Although the IT department mostly handles disaster recovery, it’s a business issue. That’s why we consider any DRP as part of the business contingency plan (BCP) — the framework for an organization’s operations during a crisis.
BCP is more general. It covers every critical area: people, facilities, suppliers, communication, and technology.
Disaster recovery fits within this framework and focuses on technology. It addresses the restoration of systems, data, and infrastructure to their original state. While BCP identifies what needs to stay operational and why, disaster recovery specifies how to keep it running.
Thus, the broader BCP should define what your DRP prioritizes and protects.
For example, if you can accept downtime of several hours, you can select slower, cheaper recovery options and not overspend on procedures that guarantee zero downtime.
However, if you run an enterprise-level business, the losses from disasters can be so significant that fast failover isn’t optional. In this case, you demand instant failover capabilities.
Key Recovery Strategies: Cost vs. Speed
There are several recovery methods, and each one differs in terms of investment required and the recovery speed you can achieve.
Backup and Restore
This is the most common and cost-effective disaster recovery method.The fundamental principle behind this strategy is that the backup data should be stored in a different location from the primary systems. For instance, if your website is hosted on Amazon Web Services (AWS), you can store the backups elsewhere, such as Hetzner or even on a local server.
Time is the major trade-off when it comes to this method. If the database is large, restoring it from the backup will take time.
This may not be feasible for businesses that lose significant amounts of money for every hour they’re offline.
Mirroring
Mirroring, also called a “hot copy,” is the most sophisticated and costly approach. It means you have a live replica of the entire project running alongside your main system. The difference is that only the main system gets user traffic. The replica environment is always updated and prepared to take over at a moment’s notice.
During a disaster, you only need to redirect traffic to the standby environment and continue operations with little or no downtime.
Although your recovery strategy largely determines both success and investment in disaster recovery, other factors also affect your results.
5 Core Disaster Recovery Planning Aspects We Rely On
Every business is unique, and so is our approach to our clients’ disaster recovery planning. However, we still rely on five core pillars in every project that ensure companies will withstand different types of threats.
Identification of Critical Systems
We start with the business side:
- What are your revenue-generating activities?
- What processes absolutely cannot stop?
- How much does an hour of downtime actually cost you?
For example, if your infrastructure is defined in code, a Kubernetes outage is less of a concern because we can quickly recreate the systems. However, if you use virtual machines, their failure can result in much more damage to your bottom line. Such details also impact the overall recovery strategy we recommend and the resources you’ll need to allocate.
Recovery Planning for Different Scenarios
Then comes the actual part—planning. As one of our engineers says, “We use our experience combined with our imagination to anticipate everything that can go wrong, from minor hitches to major disruptions.”

Armed with knowledge of your business priorities and the tech side, we create a detailed playbook that outlines the exact procedures for a variety of scenarios, such as:
- Database unavailability
- Insufficient resources for scaling or changing instance types
- Node unavailability in a cluster
- DDoS attacks
- Server failures
For instance, in the case of DDoS attacks, the recovery steps would be:
- Configure ingress to handle traffic spikes and scale up as needed
- Block malicious IP addresses responsible for the attack
- Use CDN services like Cloudflare for traffic filtering and rate limiting
- Monitor traffic patterns continuously to ensure services stay online
Our team also conducts a dry run (a simulated test of a recovery plan without actually disrupting live systems) to provide realistic estimates of how long each recovery process will take for each scenario.
In addition, we define backup frequencies. For example, critical systems might require backups every hour, while less important data can be backed up once a day or once a week.
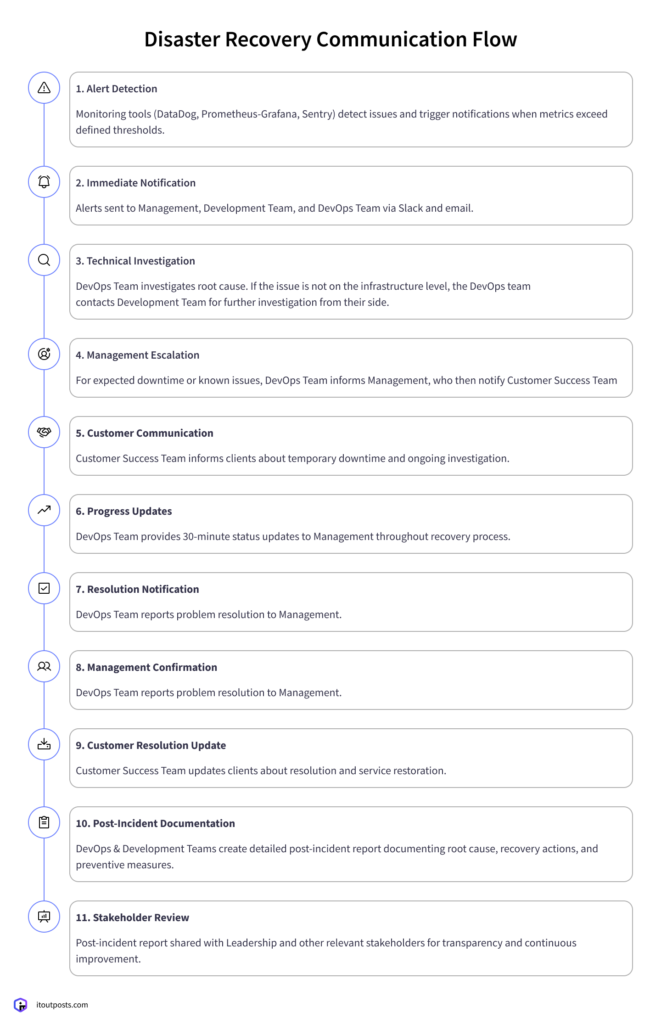
Communication Flow Plan
Communication flow matters too, as proper escalation procedures ensure the right people are notified at the right time and eliminate chaos. Here’s an example of the complete disaster recovery communication flow:
Infrastructure as Code Implementation
As DevOps professionals, we always recommend that everything should be defined in code. This Infrastructure as Code (IaC) approach means that instead of manually setting up servers, networks, databases, and security groups, all of these are described in configuration files.
This way, during a crisis when every second matters, we don’t have to search for that one person who “remembers how this works” or dig through old Slack messages for that one crucial command. We just run the code, and your infrastructure rebuilds itself.
IaC also means anyone on the team can step in and manage the project, even if the main engineer isn’t available. Plus, if the entire project is handed over to another team, they’ll have all the essential details ready, which significantly reduces onboarding time.
Regular Testing
Your business evolves over time—you add new features, connect new services, and gather more data.
That’s why it’s vital to test DRP regularly, whether that’s every month or every few months, to make sure it’s still effective.
During these tests, just like during the initial dry run, we set up a testing environment, simulate a failure, and then restore the systems. This lets us:
- Get a clear idea of how long recovery actually takes, especially as your setup becomes more complex
- Find new issues or dependencies that may have popped up since the last time we tested
- Better understand what resources you’ll need, so you can plan staffing and budgets more accurately
Stay Ahead of Disasters with AMIX
While a disaster recovery plan is essential, a well-designed architecture reduces the likelihood of disasters happening in the first place. That’s exactly what our AMIX platform is designed to do—help you build that strong foundation from the start.
AMIX is a ready-to-go architecture with over 20 tools already configured for you, complete with step-by-step guides to set up your infra.
It follows major international standards like GDPR, DORA, ISO 27001, NIST CSF, SOC 2, HIPAA, and CCPA, which significantly mitigates the impact of many potential disaster scenarios, such as data loss and regulatory penalties.
Want to give AMIX a try? Fill out the form and get it for free! You’ll only pay if you need support or specific services.

I am an IT professional with over 10 years of experience. My career trajectory is closely tied to strategic business development, sales expansion, and the structuring of marketing strategies.
Throughout my journey, I have successfully executed and applied numerous strategic approaches that have driven business growth and fortified competitive positions. An integral part of my experience lies in effective business process management, which, in turn, facilitated the adept coordination of cross-functional teams and the attainment of remarkable outcomes.
I take pride in my contributions to the IT sector’s advancement and look forward to exchanging experiences and ideas with professionals who share my passion for innovation and success.