Contents
Not everything is under our control, as some risks come from outside the system itself, with DDoS attacks being a common example. And for many businesses, these attacks have a measurable business impact. For instance, U.S. companies lose around $218,000 on average per DDoS attack, amounting to over $10 billion in losses nationwide each year.
In such cases, there’s no way to negotiate with attackers and make them stop. But what we can manage is how ready our systems are when such problems occur.
That was the position our client found themselves in.
Their platform was already operating at full speed, serving customers and generating steady revenue. But frequent DDoS attacks repeatedly disrupted their operations.
Each spike in malicious traffic meant instability in search results, and, most importantly, lost sales. The ongoing attacks kept the team in a reactive mode, as they were constantly preparing for the next disruption.
This story is about how we helped our client rethink their infrastructure, strengthening it step by step so that DDoS attacks stopped turning into outages.
The Impact of DDoS Attacks on Our Client
By the time our client reached out to us, their system was already handling a large volume of users and transactions, leaving very little tolerance for any instability. Yet, during DDoS attacks, customers couldn’t access the platform, transactions were interrupted, and sales were directly affected.
On top of that, DDoS attacks undermined our client’s SEO efforts. Since the website was frequently either slow or not accessible at all, search engines considered these failures as poor performance signals, which negatively affected search rankings and organic traffic.
This is a clear example of how technical incidents can translate into a direct business problem, since infrastructure instability didn’t just affect system metrics but disrupted sales in real time and weakened long-term traffic channels.
The Main Project Task
Stopping DDoS attacks entirely wasn’t a realistic goal. What mattered was changing how the infrastructure responded to them.
At the same time, our team identified another issue affecting day-to-day operations, beyond the DDoS attacks. The way the client’s platform was built initially didn’t let deployments happen automatically. In addition, monitoring was limited, and responding to any issues, whether DDoS or not, consumed more time and manual work than necessary.
Our Solutions
Server optimization
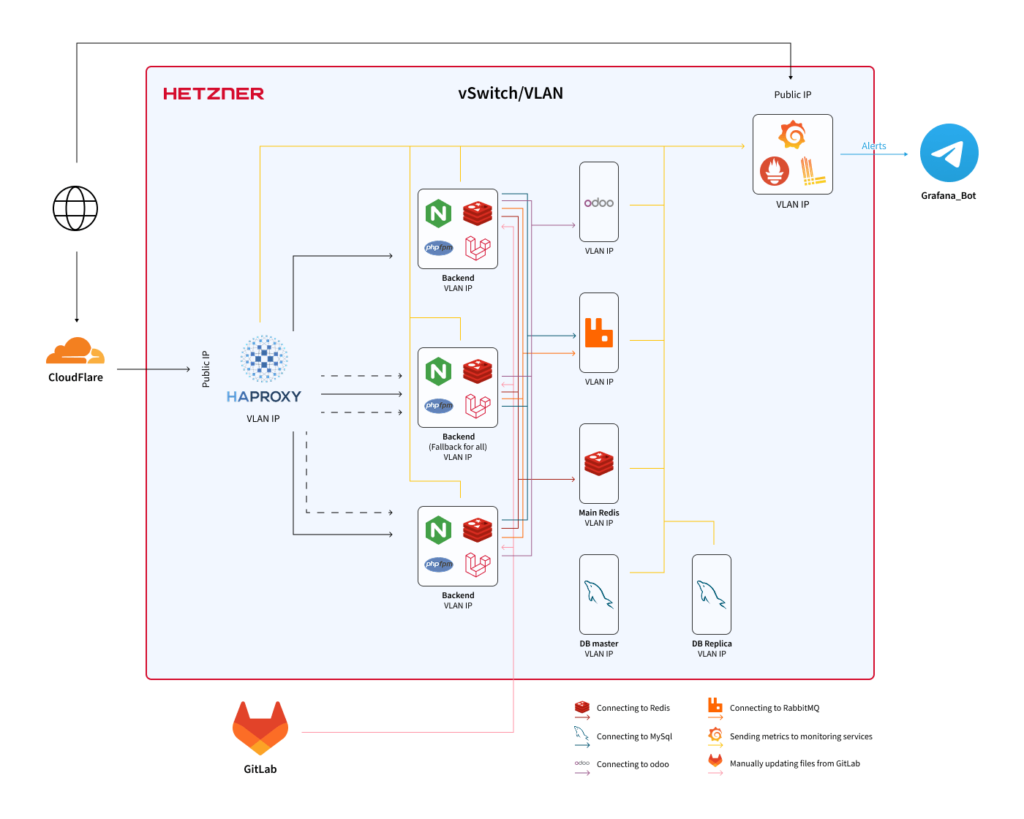
We began by strengthening the overall system to better handle heavy loads. Initially, all applications were running on a single Hetzner bare-metal server, with the database hosted on a separate server. Later, we distributed applications handling different types of traffic across three servers.
When all applications were running on a single server, there was only one Redis instance. It’s used for caching and session storage, acting as an intermediary between the application and the database.
After distributing applications across three servers, we placed Redis next to each application. However, it was important to consider that traffic between Hetzner bare-metal servers passes through network channels. These servers were connected via one-gigabit channels, and when Redis attempted to communicate with the database, it overloaded these channels. As a result, there was insufficient bandwidth left for organic traffic.
To address this, we upgraded the network channels from one gigabit to ten gigabits, which significantly improved the situation. However, because Redis instances were running independently on each application server, desynchronization issues began to occur, and clients’ customers started receiving outdated or inconsistent data.
We then decided to move Redis to a single, dedicated server. This centralized Redis instance became the primary one.
Yet, we still had to implement a backup Redis strategy, since during a DDoS attack, traffic volumes can become so large that even a ten-gigabit channel—the maximum available from the provider—can become overloaded.
To mitigate this risk, we reintroduced Redis instances on each application server but kept them disabled by default. We created a script that detects the start of a DDoS attack: when triggered, the centralized Redis instance gets disabled and the local Redis instances on each application server are enabled. This approach prevents Redis traffic from clogging inter-server communication channels and helps preserve bandwidth.
Below, you can see our server optimization solutions in greater detail
DDoS mitigation with Cloudflare
Since our client already had Cloudflare, we made full use of it. We set specific rules to prevent requests that obviously didn’t appear natural.
Database query optimization
The database was struggling with heavy, complex queries, and in the event of a DDoS attack, even 30-40 requests each second had the potential to bring down a fairly powerful server. This could occur not only during malicious attacks but also when there were genuine increases in traffic, like, for instance, during promotions or sales events. Our team conducted database query optimization.
CI/CD automation & environment setup
Next, our team set up CI/CD pipelines and created multiple environments to ensure changes could be deployed in a safe, predictable manner.
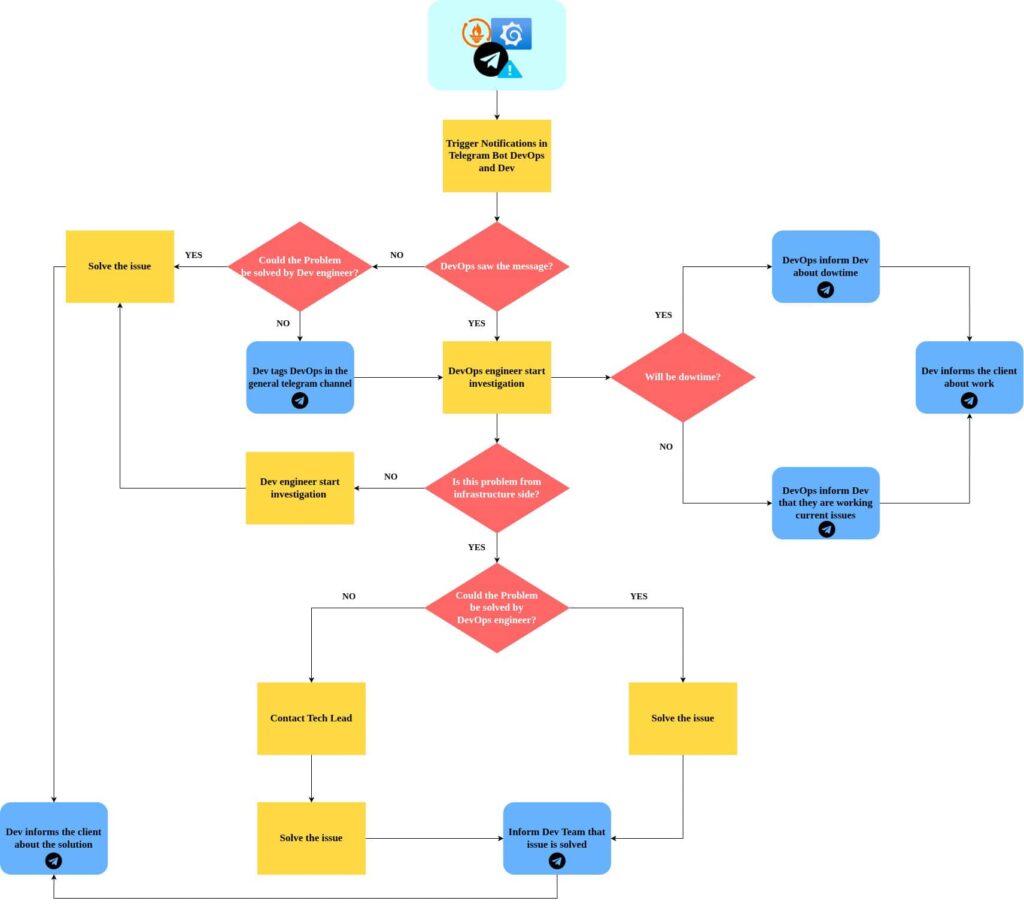
Real-time monitoring & incident alerting implementation
Becoming aware of issues and notifying about them is another important level of defense. We set up alerts for any unusual spikes in traffic. If something doesn’t look right, like an increased latency, we notice it straight away and can respond immediately.
Here’s how our incident response flowchart looks like:
Disaster recovery planning
Finally, we also created a disaster recovery plan with a clear sequence of actions for emergency situations.
Results
The biggest risk is now behind us. Our client no longer faces interruptions during DDoS attacks. In recent attacks, their platform remained completely operational—there was no noticeable impact on sales. Compared to previous incidents, the attacks were essentially invisible to customers.
With stability in place, our client’s attention has moved to more strategic objectives. We keep working on additional system enhancements, so it can better support future business growth.
Make Stability Your Default, Even Under Attack
The goal of this project was never faster reactions—it was reducing the impact of attacks altogether. It was to build an infrastructure that stays stable even when conditions aren’t. One that protects revenue, preserves visibility, and gives teams the breathing room to focus on growth.
Under DDoS pressure? If attacks are hurting your uptime and revenue, contact IT Outposts! We know how to help you regain control.

I am an IT professional with over 10 years of experience. My career trajectory is closely tied to strategic business development, sales expansion, and the structuring of marketing strategies.
Throughout my journey, I have successfully executed and applied numerous strategic approaches that have driven business growth and fortified competitive positions. An integral part of my experience lies in effective business process management, which, in turn, facilitated the adept coordination of cross-functional teams and the attainment of remarkable outcomes.
I take pride in my contributions to the IT sector’s advancement and look forward to exchanging experiences and ideas with professionals who share my passion for innovation and success.