Contents
Operating a digital business means you have to balance the speed of your team’s work and data security, which is a common challenge.
Your teams require quick, convenient access to systems to move projects forward. But, simultaneously, it’s essential to keep those very same systems protected. Not only from outside dangers such as hackers, but also from accidental mistakes inside the organization or curious users who shouldn’t have access in the first place.
That’s why a VPN is a foundational component of a robust security strategy. It lowers the risks of data leaks, streamlines audits, and more. Yet, it’s not a silver bullet — some gaps still need to be filled with other security practices. In this article, we take a closer look at what a VPN actually does for your business and how to set it up so it truly supports your team.
What Is a VPN?
A VPN, or virtual private network, is a type of technology that provides a safe and secure internet connection to a remote user from anywhere in the globe to the company’s network system. Any activities done online while operating behind the VPN are very hard to access by unauthorized users.
How Does a VPN Work?
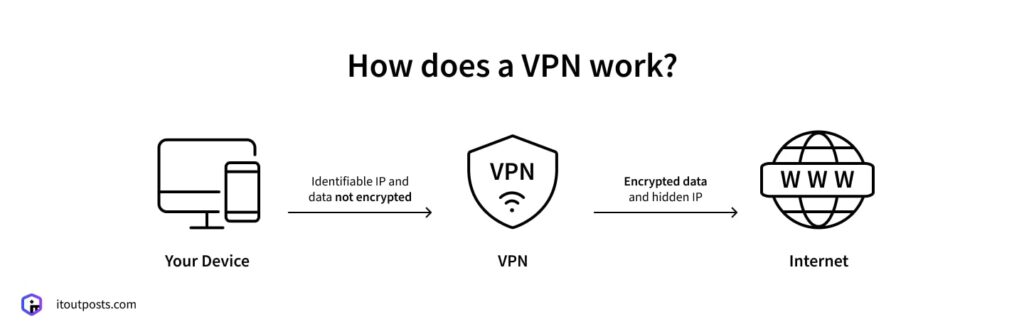
Anytime that you access the internet without a VPN, your data becomes accessible to the internet through a variety of networks, such as the Wi-Fi network and your internet service provider (ISP).
On unsecured networks like café or airport Wi-Fi, attackers can use a method called “sniffing” to gather and track the data. Even networks that appear safe, like home Wi-Fi networks and small regional ISPs, may act as weak points in the system if they aren’t properly configured. Not protected data may also include any type of sensitive data, like passwords and files being transferred.
A VPN resolves this issue by encrypting data as it travels through the internet. What this means in practice is, any data as a password or a database query, is encrypted in a layer of unreadable data before being transmitted outside an employee’s device.
If someone manages to intercept this traffic, they won’t be able to see the content. They will see a worthless stream of characters. Only the VPN server and then the company systems it connects to are able to convert the encoded data back into a readable format.
Benefits of VPN for Businesses
Most of us have used a VPN once or a few times in our lives, be it for protecting our connection to a public Wi-Fi or to access region-specific content while traveling. But how can this solution be beneficial to organizations?
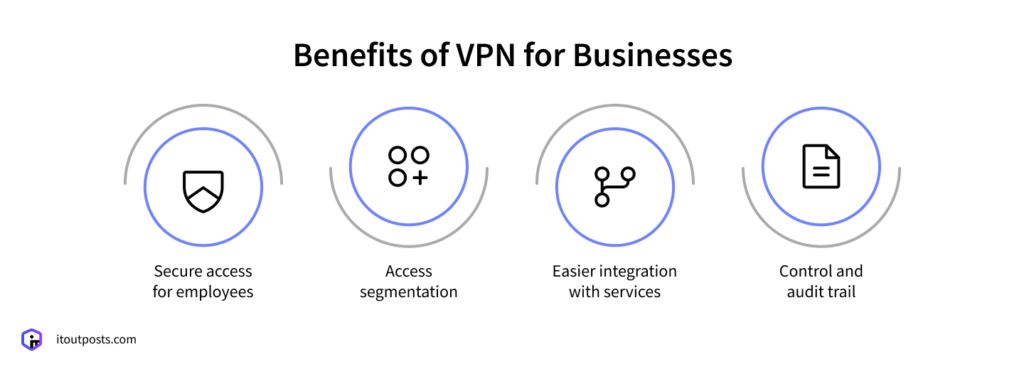
Secure Access for Employees
In the world we live in, it’s common for team members, like developers, support teams, and analysts, to be located in different parts of the world. So, the first and foremost reason for using a VPN is to allow employees to access a company’s systems (dev, staging, and production environments, databases, or internal tools) at any point in time from any corner of the globe. Securely.
Access Segmentation
Not everyone in a company needs the same level of access. Take a developer, for example, who might only need access to a dev environment, but a QA specialist or support agents need something completely different.
With a VPN, access is easily configurable to each role or team, so it’s limited to only what’s needed for the role. Even if your employees have no bad intentions, this setup protects the business from occasional mistakes, like someone accidentally changing something they shouldn’t.
Easier Integration with Services
Third-party APIs and microservices can be limited to “trusted” IP addresses, and without a VPN, it can feel impossible to manage these lists. You would have to manually include every office and every laptop. With a VPN, the management of these lists is much easier to control. You get one “trusted IP” to use for all of the integrations.
Control and Audit Trail
Along with allowing access, a VPN creates a record—You can find out who logged in, when they did it, and what device was used. These records are crucial for audits for ISO, SOC 2, and GDPR standards as they allow you to demonstrate control and compliance without having to manually gather scattered proof.
What VPN Doesn’t Solve (and Why It Needs Support From Other Practices)
Although VPN does strengthen your security, it still leaves gaps that you need to address with other practices and tools. Here’s what a VPN doesn’t cover:
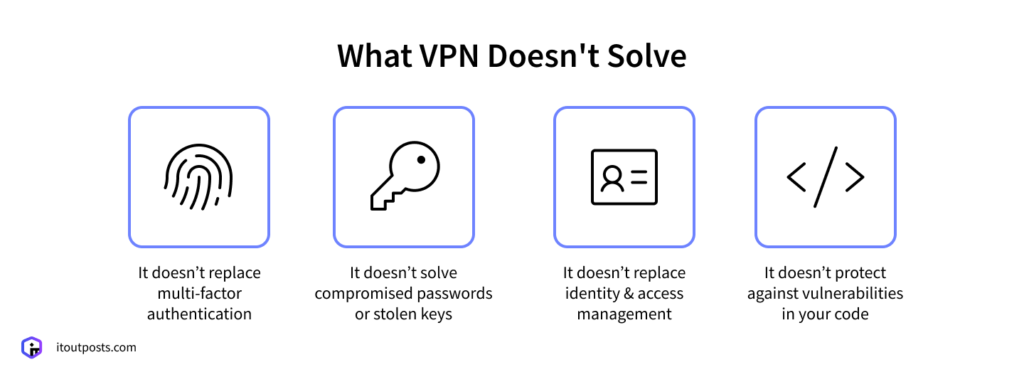
- It doesn’t replace multi-factor authentication (MFA). Having a VPN on doesn’t mean that employees shouldn’t be asked to confirm their identity using a second factor, such as a texted code or a physical token. This measure provides extra protection if a password is guessed or stolen.
- It doesn’t solve compromised passwords or stolen keys. If login details are leaked, a VPN does little to block access to these details. Password hygiene, key rotation, and monitoring are still all critical.
- It doesn’t replace identity & access management (IAM). A VPN does restrict who can connect to a network, but it doesn’t determine what actions can be taken after gaining access. IAM needs to be established independently.
- It doesn’t protect against vulnerabilities in your code. If there’s a security flaw in the product itself, a VPN won’t fix it. Regular code reviews, patching, and application security practices remain essential.
Which Industries Typically Need a VPN (and Why)
Any organization using a VPN can take advantage of the services, although some more than others, because of the nature of their business operations and the associated compliance. Below are some of these industries.
Finance and Banking
Banks, fintech startups, and insurance companies deal with highly sensitive customer and transaction data. A VPN helps protect access to core systems, trading platforms, and internal dashboards, while also ticking boxes for audits and regulatory checks like PCI DSS.
Healthcare
HIPAA in the US and GDPR in Europe mandate that clinics, hospitals, and other healthtech providers safeguard their patient information. VPNs enable nursing and other medical staff to access sensitive information and records without compromising the privacy of the patients.
Professional Services (Law, Consulting, Accounting)
Data breaches within firms dealing with sensitive legal contracts, client files, or private financial reports are costly. A VPN facilitates secure remote connections, particularly abroad or outside the office, for partners and employees managing client cases.
Manufacturing and Logistics
Factories and logistics platforms are often built on interconnected systems ranging from supply chain dashboards to IoT devices. VPNs offer enhanced perimeter control to ensure that only authorized staff and contractors can access these systems.
What Does It Take to Get VPN Right?
By itself, a VPN is just a tool. The strategy wrapped around it is what gives it business value. What does this look like in action? The following are the basic steps that allow a VPN to function within your business environment correctly.
Designing the Setup
First, there’s the design question:
- Who should be able to get in?
- What areas should they be allowed to access?
- What devices should users be allowed to use?
Answer these questions upfront to have a clear access map you can then use when configuring your VPN setup.
Choosing the Right Tech
Then comes the choice of technology. Do you go with OpenVPN, WireGuard, or a cloud VPN from AWS, GCP, or Azure? There’s no universal answer. It depends on the way your company is structured and your existing tech stack.
Connecting with Your IAM Tools
You’re most likely already using AWS, Google Workspace, or Azure AD for identity access management. Your VPN should integrate directly with those. This way, access updates automatically whenever someone new joins and leaves.
Automating Access
Manually adding and removing people might work for five employees. But what is there are fifty or even more? In this case, consider infrastructure as code (IaC) tools like Terraform or Ansible. These will enable you to give out (and take back) VPN access in seconds.
Ensuring You Scale Confidently
New employees, new teams, new services: these are all part of a growing business. An excellent VPN setup is one that grows with your business effortlessly.
Get VPN Right with IT Outposts
At IT Outposts, a trusted DevOps partner, we believe security shouldn’t feel like a roadblock. Our goal is to make VPNs and the access model around them reliable and scalable.
Contact us and make system access one less thing to worry about!

I am an IT professional with over 10 years of experience. My career trajectory is closely tied to strategic business development, sales expansion, and the structuring of marketing strategies.
Throughout my journey, I have successfully executed and applied numerous strategic approaches that have driven business growth and fortified competitive positions. An integral part of my experience lies in effective business process management, which, in turn, facilitated the adept coordination of cross-functional teams and the attainment of remarkable outcomes.
I take pride in my contributions to the IT sector’s advancement and look forward to exchanging experiences and ideas with professionals who share my passion for innovation and success.