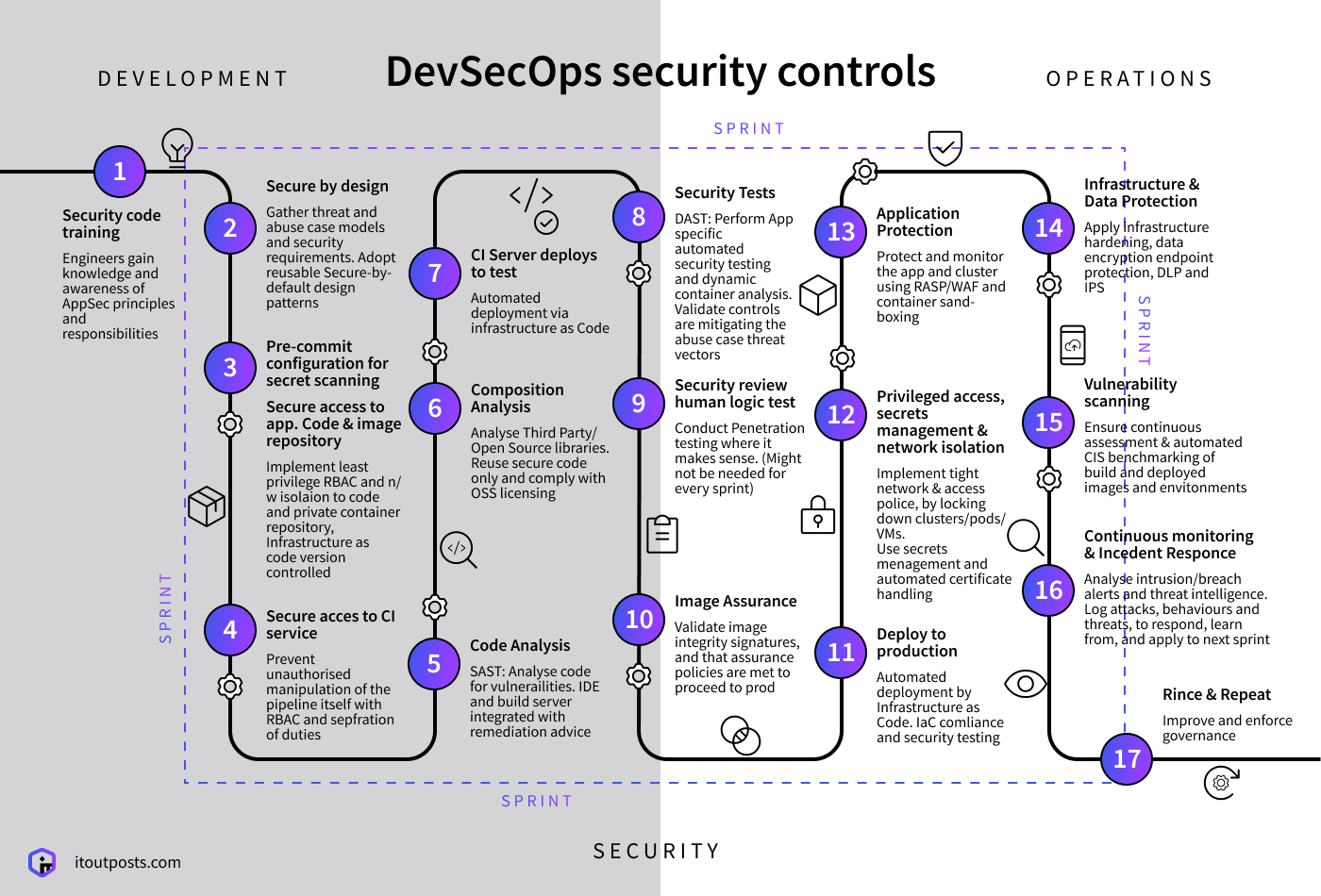
Contents
Do you still have some concerns about getting DevOps involved in your application? Are you afraid that DevOps tools will make your project vulnerable to hacker attacks, harming the reputation of your business? Can you use their tools and at the same time avoid the risk of being hacked? In this article, you will learn about the risks of working with DevOps and get security consultancy services to overcome them.
What is DevOps Security?
Like DevOps, which stands for Developers and Operations, DevSecOps or DevOps Security stands for Operations, Security, and Development. DevOps Security is the specialized practice of protecting your code and commercial secrets from hackers. You may ask, can DevOps protect my project? What are the main risks involved?
What are DevOps security risks?
The ‘Privileged Access Management’ tool is attractive to hackers
DevOps use a special tool called Privileged Access Management. This software requires that the user enter special credentials to get access to the source. It is very similar to your email, or your LinkedIn account; when you want to log in, you need to enter your username and password. Privileged Access Management works in the same way.
Hackers across the world are always looking for opportunities to steal your passwords and get access to your accounts (and we hope it will never happen!) If hackers successfully break into your DevOps team’s tools, they will steal passwords, access keys, SSH keys and tokens, certificates, encrypted and API keys. They can simply destroy your intellectual property or crack your data.
Read also: DevOps security integration
Many DevOps are focused on speed
It is important to choose your DevOps team carefully because some DevOps companies prioritize speed, not security. Imagine yourself as a driver in a high-speed car race. You want to win the race by being fast, yet safe. But you find yourself surrounded by many other drivers who just want to win. They press on the gas without worrying about safety and are happy to make risky moves – endangering themselves and the other drivers – to win the race.
Likewise, many DevOps teams just focus on producing code fast, not giving proper attention to security issues. This includes leaving embedded secrets and credentials in application and configuration files, reusing third-party codes, and installing new tools without evaluating its potential risks.
Many different tools create security gaps
DevOps engineers mix together software that shares secrets across tools, clouds, and platforms. But this complicates the job of the security team. In a similar way, I have accounts spread across a range of different websites. Since I cannot remember all the passwords in my head, I write them all down in a book. But if I lose that book, I will lose control over the situation. If I had only one service it would be easy to remember, but since I use many different accounts, I must write down passwords.
Read also: Six challenges of DevOps adoption
How can I overcome these risks?
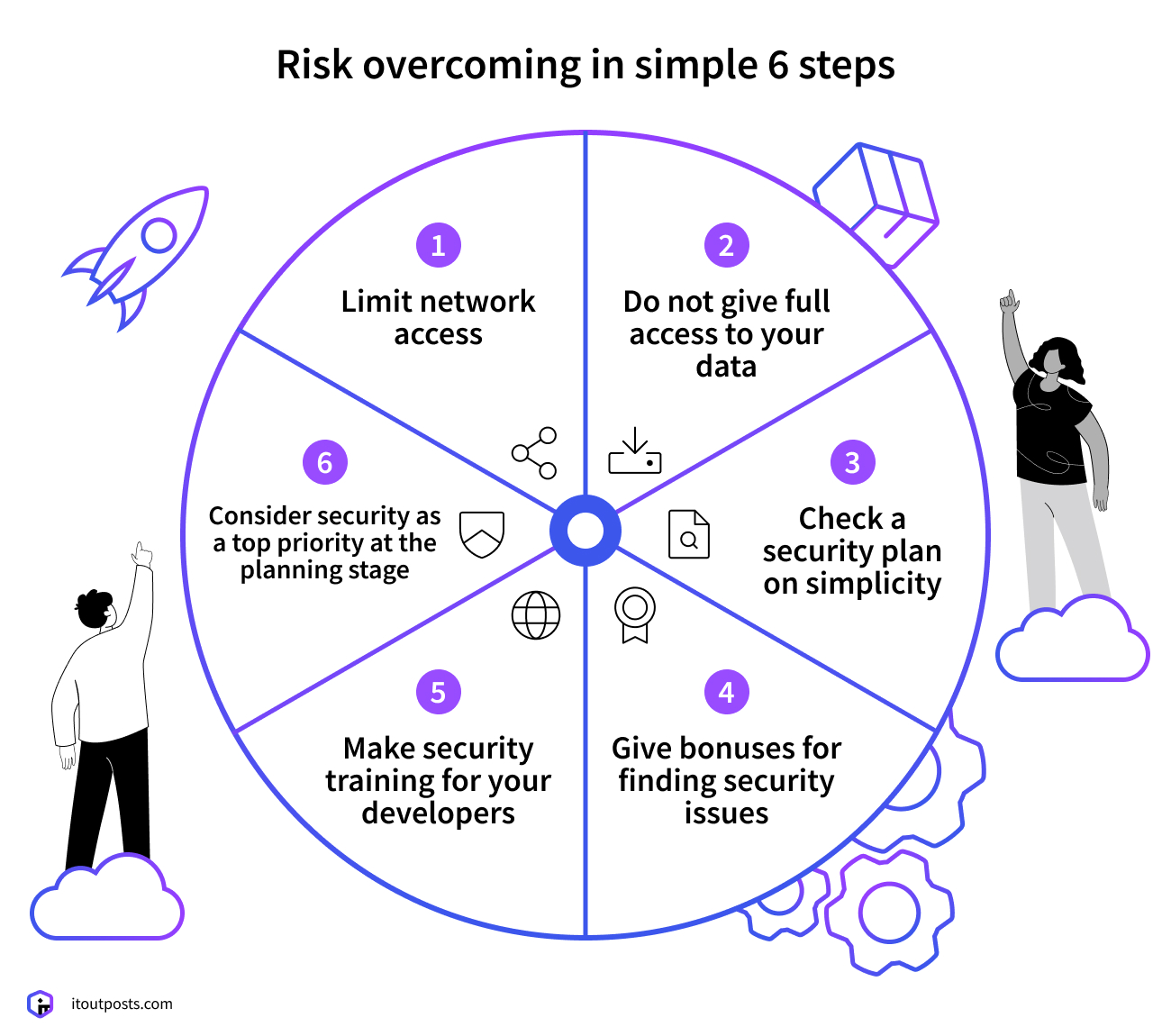
Treat security as a top priority at the planning stage
Check that your DevOps team comes with a clear and transparent cybersecurity policy that you fully understand and with which you agree. It is much cheaper to discover and fix vulnerabilities at this early stage than later on. Make sure that the DevOps team runs automated security tests early and everywhere in your application.
Moreover, investigate IT Outposts’ DevOps Managed Services and also, take a look at DevOps Outsourcing Services.
Engage in security training for your developers
Find time and resources for your developers to take part in security training. This is a great idea because this investment in education will save lots of time and resources later on, and maybe even save your business. Your developers will know how to secure the code and create fewer opportunities for hackers to ruin your business.
Read also: Seven threats of cloud migration
Give bonuses for finding security issues
Besides security training, which is very important, consider a system of rewards for your employees. To really motivate your staff, pay them a bonus per any vulnerability they find.
Make sure your security policy is easy to understand
Complexity is the enemy here! Check that your DevOps documentation is simple. You should have a WISP (written information security plan) and a DIRP (data incident response plan). Your main goal is to check if it is clear and concise, simple enough that you can always keep all of it in your head. When these documents are more than a couple of pages, they are useless. Moreover, they become obstacles because you cannot remember all the text.
You might be interested in: DevOps Trends</p.
Do not grant full access to your data
If you have a big project, you do not need to give your whole team full access to your data all the time. Consider limiting data access, using time limits, and giving team members access only to the parts of your project that are necessary at that time. Reducing the number of people accessing your data will limit the risk of hacks or leaks.
Limit network access
All security policies are great on the paper, but how about in practice? Ask what the DevOps team does to prevent attacks, protect the code, and control third-party access. Consider limiting the number of users allowed to access the network. It is better to be safe than risk suffering from data breaches or lost income.
Before signing a contract with DevOps, check their security policy, access and network security, certifications, physical and human resource security, and regular risks assessment.
More to explore: AWS Security Consulting Services
You do cannot be sure of anything until you test it
You may think that you can fly until the moment you jump off the roof. Likewise, you may think your application is safe and ignore warnings until you release it into the wild. DevOps are a comparably new force on the market and many of these teams do not give their full attention to security issues. So before choosing a DevOps team, check if they can cover all security risks associated with your business.
Fill the Сontact form below and get the estimation of your project absolutely for FREE
FAQ
Is Azure DevOps secure?
Yes, all data is encrypted, and access is only opened to specific people.
What are some great tools for integrating security into DevOps?
Jenkins/Hudson, TravisCI, or Anthill Pro.
How do you apply DevOps principles to make a system secure?
Bring the security team in from the very beginning.

I am an IT professional with over 10 years of experience. My career trajectory is closely tied to strategic business development, sales expansion, and the structuring of marketing strategies.
Throughout my journey, I have successfully executed and applied numerous strategic approaches that have driven business growth and fortified competitive positions. An integral part of my experience lies in effective business process management, which, in turn, facilitated the adept coordination of cross-functional teams and the attainment of remarkable outcomes.
I take pride in my contributions to the IT sector’s advancement and look forward to exchanging experiences and ideas with professionals who share my passion for innovation and success.